5 Best Ways to Protect a PDF File from access & viewing
How to protect your PDF files from viewing & which solution is best.
This blog ranks the various solutions that claim to protect PDFs from viewing and unauthorized access and explain why some of them may not be as effective as you would expect.
The PDF file format has a long history, but it is one that is unfortunately marred by security vulnerabilities, flaws, and cracks. While at the time of writing some of the more serious issues have been remedied, more are routinely discovered across the specification’s various versions. In 2022 there are still various ways for hackers to exploit PDFs, enabling both the injection of malicious code and opening of documents thought to be safely encrypted by Adobe Acrobat.
Given Adobe’s track record, these are not issues that are likely to be remedied soon. In fact, the password-based model the company has chosen for its PDF format, while convenient, will always be flawed. Passwords are just too easy to purposefully share, crack, social engineer, or phish, and the permissions password used to restrict use can be instantly removed with a free online tool – see how secure is Adobe encryption? Clearly, Adobe password protection is not a good way to protect PDF files from being accessed or viewed without your permission.
 | Other document security solutions to avoid that can restrict PDF access & viewing |

If Adobe password protection is useless, what can be used instead? Here are a few alternatives that can be used to protect a PDF file but that didn’t make the list. It’s worth quickly covering the problems with these solutions so that you don’t fall into the trap of purchasing them:
Secure data rooms
Access to secure data rooms is granted through passwords, which presents the exact same issues as Adobe Acrobat – password sharing. Secure portals are also accessed via the web browser, using JavaScript for protection which can be easily bypassed. It therefore does not have enough control to be able to restrict the extraction of information which can then be delivered to third parties.
Cloud storage services
Cloud storage services let you restrict access to a PDF to a specific user on that service. One example of this is Adobe Cloud security, which supports security mechanisms such as RBAC. The problem again is that the user can still share their login information and can easily extract and share the information via screenshots, JavaScript manipulation, temporary files, or printing to a PDF.
Microsoft Word protection
Microsoft Word lets you open PDF files and then encrypt them against opening in the .docx format. However, it has the same problem as Adobe Acrobat – users can just share the open password to the document or the unprotected document once they have decrypted it. Word’s editing protection is easy to bypass, so you also cannot stop users from copying the text and pasting it wherever they like.
Gmail confidential mode
Though its name implies protection for confidential information, Gmail confidential mode is really just a poorly thought-out email expiry tool. Though it claims to disable copying, forwarding, printing, and downloading, this is easily bypassed by ticking a few boxes in Firefox’s style editor of right-clicking the page and pressing “Save as”. It also does not support end-to-end encryption and deleted emails are not fully deleted.
Google Docs
Google Docs is an excellent collaboration tool, and is meant to prevent editing, copying & printing. But it relies on JavaScript to protect files and a password based login. Google Docs security is easy to bypass by just amending the URL in the browser and disabling JavaScript to remove the restrictions.
PDF download prevention solutions
There are several WordPress plugins and other solutions that claim to prevent the download of PDFs from web pages. They usually do this by embedding the PDF into the webpage and removing the print and download options. You can probably guess by now that this is not effective at all. There are many easy ways to bypass this, as covered in using WordPress for secure sharing of PDF files.
So, if these solutions are unsuitable, what should you be using to protect your PDFs from unauthorized access and viewing? We’ll look at the five best methods on the market and explain why the situation may be more complicated than you think.
 5. PGP File Encryption
5. PGP File Encryption
Simple PGP encryption is a good, free way to limit the chances that a sensitive file can be viewed when it’s in transit or not being used. It utilizes a combination of symmetric and public key encryption to enable the exchange of encrypted files without the need for users to share their private encryption keys.
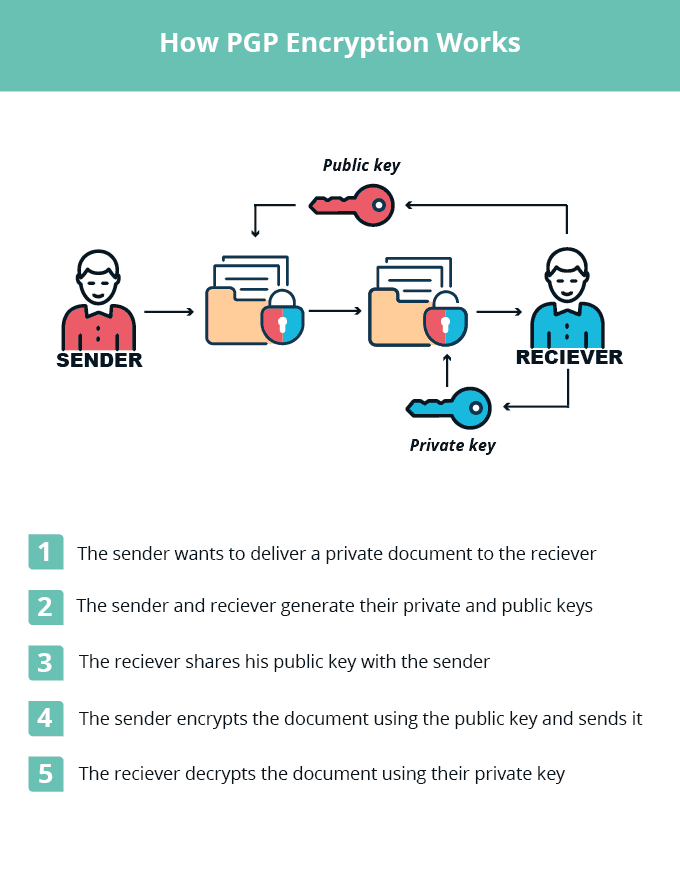
Though users can have their private keys stolen, they are far longer and more complex than passwords and there are few legitimate reasons to send a private key to somebody else. This makes them very difficult to crack and quite resistant against phishing or social engineering attacks.
PGP file encryption is far from perfect, however. A “rogue” user who is authorized to open the document could just share the decrypted version of the document.

To put it simply: file encryption does not protect a document after it has been decrypted. Once a user has opened it, they can do whatever they like with it. For that reason, unauthorized users may still end up viewing your confidential document. This is why we primarily recommend file encryption’s use in combination with one of the tools below, rather than as a standalone solution.
 4. Access control systems
4. Access control systems
Access control systems like Windows Active Directory are generally quite effective at preventing users who shouldn’t have access to documents from viewing them. For the uninitiated, they consist of a set of services that run on Windows Server and manage access to networked resources such as computers, files, and printers. They can be further bundled with document encryption tools so that files remain protected in transit and at rest.

Essentially, the access control system checks a user’s credentials when they try to access, modify, copy, or execute a file. The limitations are built into the operating system and are difficult to bypass, which makes them a good starting point for many enterprises.
However, they aren’t perfect either. Users who do have permission to view, modify, and transfer files can still leak the information to others. You only have to look at Edward Snowden to see how this can happen even at the highest levels.
Access control is also fundamentally an internal system. There’s no mechanism to securely share information with those outside your system, as your IT admins do not have the requisite control over their operating system. This can also make access control difficult to enforce in bring-your-own device (BYOD) and work-from-home environments. For most modern enterprises, this makes access control unsuitable.
 3. Enterprise Rights Management (ERM) systems
3. Enterprise Rights Management (ERM) systems
Enterprise Rights Management (ERM) systems share similarities to access control systems but have some distinct advantages. Let’s take Microsoft’s Azure Information Protection (AIP) as an example. A cloud-hosted, policy-driven system, it works by allowing admins to assign classifications to documents and define policies and optionally add document protection via Azure RMS to those files.
Due to its cloud-based nature, AIP can support mobile and BYOD devices, on-premises directories, cloud authentication, SharePoint, Exchange, etc., and track and revoke Office 365 documents. This makes it suitable for everyday enterprise use, but it does still have some drawbacks.

As well as being a complex method of file protection, it is costly to set up and maintain, supports only a limited number of file formats (primarily those by Microsoft and Adobe), and doesn’t currently have a client for macOS.
Additionally, though it is possible to share with external parties, it still wasn’t designed for it. The receiver must have the latest version of Office 365 or download a dedicated AIP client, make an account, and install it with admin privileges. The exact sign-up process for the end user further varies depending on what account type they’re using, leading to confusion and mistakes like end users signing up for an MSA account with an enterprise domain.
This is made worse by the fact that adding an external contact to the system is quite fiddly for admins. This is especially for users with corporate domains, where AIP creates an orphaned domain in Azure AD, and admins must go through a convoluted process that includes PowerBI signup to perform a domain takeover.
In other words, the external sharing process is just a headache on all sides. ERM systems are also just overkill for some businesses. If you primarily need to protect PDF files, paying out for a fully-fledged ERM system and the IT expertise required to utilize doesn’t make sense. Especially since Microsoft Rights Management can be manipulated – users with view access can gain bypass document restrictions enabling copies to be made without any restrictions.
 2. Safeguard PDF Security
2. Safeguard PDF Security
Safeguard PDF security provides a simple yet effective way to protect a PDF file from viewing, unauthorized sharing, copying, editing, and printing. There are no passwords to enter or remove, insecure plugins, or weak JavaScript protection. It trades complex policy-based systems for a combination of encryption, Digital Rights Management (DRM) controls, transparent licensing, and a secure viewer application. In doing so, it is able to prevent unauthorized viewing regardless of whether the user is internal or external, at a reasonable cost with low overheads.

Here are just 5 ways that Safeguard protects PDF files to prevent unauthorized access, viewing, and use.
Restrict PDF access without passwords
No passwords mean nothing for users to share or remove, either intentionally or via a phishing or social engineering attack. Locklizard securely and transparently relays decryption keys to an encrypted keystone that cannot be shared.
Preventing sharing
Lock use to specific devices through licensing controls to ensure that files copied, emailed, or forwarded to another device will not open.
Preventing copying
- Files copied to another device are useless without the requisite license files and decryption keys, which can only be obtained by authorized users.
- The Safeguard PDF Viewer stops copy & paste so that text and images cannot be copied to another app.
- Safeguard grays out the viewer window when a first or third-party screen-grabbing tool or VM is used to prevent copying via images (unless otherwise specified). You can also choose the blank out the window when it is not in focus to stop users from manually typing the content in another document.
- Dynamic watermarks prevent users from easily duplicating content by OCR in scenarios where screenshots or printing is allowed.
- Safeguard contains no editing functionality and as a result, users cannot remove watermarks or make unsanctioned changes to documents.
Preventing printing
Admins can stop printing entirely to prevent the scanning and OCR processing of printed copies, limit the number of prints per user, or only allow black and white copies.
Preventing saving
Safeguard Viewer has no “Save As” function and saving a copy by printing to a file driver is also not possible. This stops users from viewing the document in a different application.
The key takeaway is that Safeguard DRM does more than just prevent the opening of files. It stops authorized users from copying, printing, saving, editing, or screenshotting content and giving it to someone else to view. To prevent sharing, PDF files are locked to authorized devices and will not work if copied to other devices. You can also instantly revoke files regardless of their location, or expire them on a specific date or after a period of time, opens or prints.
Finally, dynamic watermarks enable you to protect a document once yet maintain the ability to add personalized information to each copy of the document. Inputting the %email% and %username% variables, for example, will cause the email and name of the user to be inserted into the watermark at open or print time (if printing is allowed).
 1. Safeguard Enterprise PDF DRM
1. Safeguard Enterprise PDF DRM
Safeguard Enterprise PDF DRM builds on the features of Safeguard PDF security. It offers all of the features mentioned above, plus the ability to track PDF document views and prints, restrict access to IP addresses and countries, generate reports, and more.

Both versions of Safeguard can also be extended by add-ons for additional automation and customization. As well as a fully offline USB PDF distribution mechanism, organizations can benefit from e-commerce integration, which automatically adds users or customers to the admin system when they sign up. A command-line tool may then be used to automatically protect or batch-protect documents, reducing the management overhead even further.
 The bottom line
The bottom line
What should be clear at this point is that preventing opening is not the same as preventing viewing. To protect a PDF from viewing, you also need to make sure that authorized users cannot create copies of PDF files and share them instead.
Solutions that can do this while maintaining an easy way of sharing confidential documents securely with users outside of the internal network are few and far between. There are ultimately two real choices: an Enterprise Rights Management system or a Document Rights Management system. For most, PDF DRM will be the natural choice as it is provides superior protection, is cost-effective, and far less complex.
To protect your PDF files from unauthorized viewing, sharing, copying, editing, and printing, take a 15-day free trial of our PDF DRM software.

 5. PGP File Encryption
5. PGP File Encryption 4. Access control systems
4. Access control systems 3. Enterprise Rights Management (ERM) systems
3. Enterprise Rights Management (ERM) systems 2. Safeguard PDF Security
2. Safeguard PDF Security 1. Safeguard Enterprise PDF DRM
1. Safeguard Enterprise PDF DRM The bottom line
The bottom line